Security
Functional Synology DSM 7.0 VPN Server
by dervish on Jul.10, 2022, under Apple, iOS, iPhone, Linux, Security
Synology VPN Server
Forward ports 500, 1701, 4500 to server
VPN Server: Enable L2TP/IPSec, confirm Authentication is MS-CHAP v2, and set pre-shared key, enable user permissions for L2TP
IPad/IPhone VPN Client: L2TP w/ secret
Windows VPN Client: L2TP/IPSec with pre-shared key
Windows VPN Adapter Options:
Set VPN adapter Security Tab to Layer 2 Tunneling Protocol with IPSec (L2TP/IPSec)
Set Requires encryption (disconnect if server declines)
Set “Allow these protocols” and enable Microsoft CHAP Version 2 (MS-CHAP v2)
Adobe patches actively exploited Flash Player vulnerability in 24 flaw fix | PCWorld
by dervish on Apr.08, 2016, under Security
Adobe Systems released a security update for Flash Player to fix 24 critical vulnerabilities, including one that hackers have been exploiting to infect computers with ransomware over the past week.
Source: Adobe patches actively exploited Flash Player vulnerability in 24 flaw fix | PCWorld
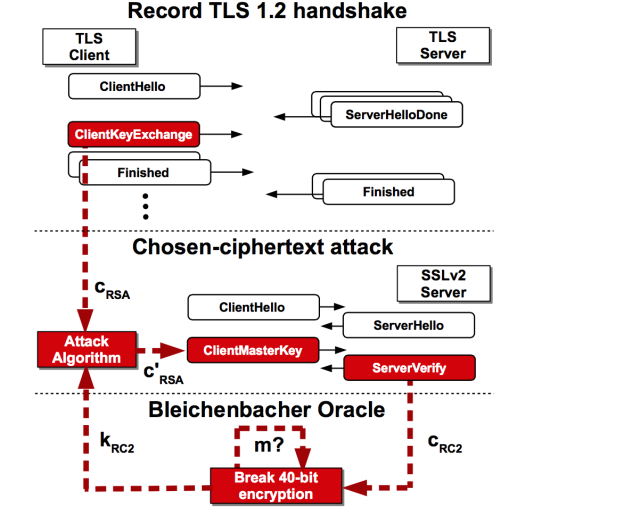
More than 11 million HTTPS websites imperiled by new decryption attack | Ars Technica (DROWN)
by dervish on Mar.01, 2016, under Security
More than 11 million websites and e-mail services protected by the transport layer security protocol are vulnerable to a newly discovered, low-cost attack that decrypts sensitive communications in a matter of hours and in some cases almost immediately, an international team of researchers warned Tuesday. More than 81,000 of the top 1 million most popular Web properties are among the vulnerable HTTPS-protected sites.
Source: More than 11 million HTTPS websites imperiled by new decryption attack | Ars Technica
SSL 3.0 Protocol Vulnerability and POODLE Attack | US-CERT
by dervish on Oct.17, 2014, under Security
Systems AffectedAll systems and applications utilizing the Secure Socket Layer (SSL) 3.0 with cipher-block chaining (CBC) mode ciphers may be vulnerable. However, the POODLE (Padding Oracle On Downgraded Legacy Encryption) attack demonstrates this vulnerability using web browsers and web servers, which is one of the most likely exploitation scenarios.Some Transport Layer Security (TLS) implementations are also vulnerable to the POODLE attack.
Source: SSL 3.0 Protocol Vulnerability and POODLE Attack | US-CERT
Heartbleed bug: What you need to know (FAQ) – CNET
by dervish on Apr.11, 2014, under Security
The Heartbleed bug, a newly discovered security vulnerability that puts users’ passwords at many popular Web sites at risk, has upended the Web since it was disclosed earlier this week. It’s an extremely serious issue, and as such, there’s a lot of confusion about the bug and its implications as you use the Internet.